NET::ERR_CERT_REVOKED <= This is an error I got when connecting to the Cups Admin page see the heading below "How to fix NET::ERR_CERT_REVOKED"
Work-a-round: You can just use Safari and add the cert to the local trust list or see the heading below "How to fix NET::ERR_CERT_REVOKED"
Some helpful commands to be able to work with Cert from the command line with openssl https://www.sslshopper.com/article-most-common-openssl-commands.html
Generating a new cert with default settings doesn't fix the problem
The following on its own didn't work. See the heading below for the fix.
openssl req -new -x509 -keyout server.key -out server.crt -days 700 -nodes -config openssl.cnf
mv server.key /etc/cups/ssl/<CurrentKey>
mv server.crt /etc/cups/ssl/<CurrentCert>
# e.g
mv server.crt /etc/cups/ssl/62745392ddb7.crt
mv server.key /etc/cups/ssl/62745392ddb7.key
#restart cups
But the above generated the following cert that is a problem still
-----BEGIN CERTIFICATE-----
MIID9zCCAt+gAwIBAgIULVQ022StQy8qJGxKJUvJ8HqQlgIwDQYJKoZIhvcNAQEL
BQAwgYoxCzAJBgNVBAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQK
DBhJbnRlcm5ldCBXaWRnaXRzIFB0eSBMdGQxDTALBgNVBAsMBGhvbWUxEDAOBgNV
BAMMB3Rlc3R3bXMxIjAgBgkqhkiG9w0BCQEWE2phbWVzQHRvZ2dlbi5jb20uYXUw
HhcNMTkxMjEzMDYwNzM3WhcNMjExMTEyMDYwNzM3WjCBijELMAkGA1UEBhMCQVUx
EzARBgNVBAgMClNvbWUtU3RhdGUxITAfBgNVBAoMGEludGVybmV0IFdpZGdpdHMg
UHR5IEx0ZDENMAsGA1UECwwEaG9tZTEQMA4GA1UEAwwHdGVzdHdtczEiMCAGCSqG
SIb3DQEJARYTamFtZXNAdG9nZ2VuLmNvbS5hdTCCASIwDQYJKoZIhvcNAQEBBQAD
ggEPADCCAQoCggEBAM6ui4Bq5bfYLR953c146MNNX7qxbGx4rXafpv/Noq67TiGK
rZ5zmV77lR96e9dfRGtpi2qSlQFovdHYka5odxh2IHHGoCsD+ZbtWNLin9Yz+BoE
ESur4/KkEEysIBsVsDm6lnpvmvafbqDwlqRhRPVnvU7kDOp8kz499fsvX4dpVwK5
joJ4SwTSgIl7oyxK2srQUUiByxeD0Y1An/TWBzGsHIO+NKCcu7bZhlMInbyLwidm
4LYY1rHXrUb+xjBBz4/JQk5Tb9V2p+R25zvGcSCAVNuSqUmWv1ptsYkcao9vSA/D
7YuX6FccV92jEH8EYNHm87r+8/O6L+ZS/3FCq5UCAwEAAaNTMFEwHQYDVR0OBBYE
FGxe+T/gfAwEYqjRh0KtILZa2nVOMB8GA1UdIwQYMBaAFGxe+T/gfAwEYqjRh0Kt
ILZa2nVOMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAJQqCScd
K+rgTw+fFanEPSnpleuIMHTOLSylK+XmYFE0j95EGe3h8wpBD53yoJ7ADoDz0psJ
F9Y+4u93zT6JKB7TcMd2jzohfrMqxPjgDnxMpJthFJRjJsS/ZqF7iuDthdpg/2Ii
XjxG/5ujss6UOkLgHsABXjUt/SRWGMt+wNVfNY7F88mWFWLFoLxOvLaZv3Vq7Q8K
EF+lbBgVj4GMsZRlFx3vwYKb/AW6PFCkfC6rIyBQDSOP3z85c+jqftQ2oqdTL2cg
1JqPUnA/NN8I4TUiQp+ZMEM4/wDNgI1SZg0wgchJje0dRTeNrIfwo8VcF0KKy3RO
xP6IyMfdYD1V+lo=
-----END CERTIFICATE-----
The above cert which throws NET::ERR_CERT_REVOKED in Google Chrome shows the following when run through Chrome
root@62745392ddb7:/etc/cups/ssl# openssl x509 -in 62745392ddb7.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
2d:54:34:db:64:ad:43:2f:2a:24:6c:4a:25:4b:c9:f0:7a:90:96:02
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = AU, ST = Some-State, O = Internet Widgits Pty Ltd, OU = home, CN = testwms, emailAddress = [email protected]
Validity
Not Before: Dec 13 06:07:37 2019 GMT
Not After : Nov 12 06:07:37 2021 GMT
Subject: C = AU, ST = Some-State, O = Internet Widgits Pty Ltd, OU = home, CN = testwms, emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:ce:ae:8b:80:6a:e5:b7:d8:2d:1f:79:dd:cd:78:
e8:c3:4d:5f:ba:b1:6c:6c:78:ad:76:9f:a6:ff:cd:
a2:ae:bb:4e:21:8a:ad:9e:73:99:5e:fb:95:1f:7a:
7b:d7:5f:44:6b:69:8b:6a:92:95:01:68:bd:d1:d8:
91:ae:68:77:18:76:20:71:c6:a0:2b:03:f9:96:ed:
58:d2:e2:9f:d6:33:f8:1a:04:11:2b:ab:e3:f2:a4:
10:4c:ac:20:1b:15:b0:39:ba:96:7a:6f:9a:f6:9f:
6e:a0:f0:96:a4:61:44:f5:67:bd:4e:e4:0c:ea:7c:
93:3e:3d:f5:fb:2f:5f:87:69:57:02:b9:8e:82:78:
4b:04:d2:80:89:7b:a3:2c:4a:da:ca:d0:51:48:81:
cb:17:83:d1:8d:40:9f:f4:d6:07:31:ac:1c:83:be:
34:a0:9c:bb:b6:d9:86:53:08:9d:bc:8b:c2:27:66:
e0:b6:18:d6:b1:d7:ad:46:fe:c6:30:41:cf:8f:c9:
42:4e:53:6f:d5:76:a7:e4:76:e7:3b:c6:71:20:80:
54:db:92:a9:49:96:bf:5a:6d:b1:89:1c:6a:8f:6f:
48:0f:c3:ed:8b:97:e8:57:1c:57:dd:a3:10:7f:04:
60:d1:e6:f3:ba:fe:f3:f3:ba:2f:e6:52:ff:71:42:
ab:95
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
6C:5E:F9:3F:E0:7C:0C:04:62:A8:D1:87:42:AD:20:B6:5A:DA:75:4E
X509v3 Authority Key Identifier:
keyid:6C:5E:F9:3F:E0:7C:0C:04:62:A8:D1:87:42:AD:20:B6:5A:DA:75:4E
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
94:2a:09:27:1d:2b:ea:e0:4f:0f:9f:15:a9:c4:3d:29:e9:95:
eb:88:30:74:ce:2d:2c:a5:2b:e5:e6:60:51:34:8f:de:44:19:
ed:e1:f3:0a:41:0f:9d:f2:a0:9e:c0:0e:80:f3:d2:9b:09:17:
d6:3e:e2:ef:77:cd:3e:89:28:1e:d3:70:c7:76:8f:3a:21:7e:
b3:2a:c4:f8:e0:0e:7c:4c:a4:9b:61:14:94:63:26:c4:bf:66:
a1:7b:8a:e0:ed:85:da:60:ff:62:22:5e:3c:46:ff:9b:a3:b2:
ce:94:3a:42:e0:1e:c0:01:5e:35:2d:fd:24:56:18:cb:7e:c0:
d5:5f:35:8e:c5:f3:c9:96:15:62:c5:a0:bc:4e:bc:b6:99:bf:
75:6a:ed:0f:0a:10:5f:a5:6c:18:15:8f:81:8c:b1:94:65:17:
1d:ef:c1:82:9b:fc:05:ba:3c:50:a4:7c:2e:ab:23:20:50:0d:
23:8f:df:3f:39:73:e8:ea:7e:d4:36:a2:a7:53:2f:67:20:d4:
9a:8f:52:70:3f:34:df:08:e1:35:22:42:9f:99:30:43:38:ff:
00:cd:80:8d:52:66:0d:30:81:c8:49:8d:ed:1d:45:37:8d:ac:
87:f0:a3:c5:5c:17:42:8a:cb:74:4e:c4:fe:88:c8:c7:dd:60:
3d:55:fa:5a
How to fix NET::ERR_CERT_REVOKED
Using this information here https://openwrt.org/docs/guide-user/luci/getting_rid_of_luci_https_certificate_warnings
Also a good scripted example and explanation here: http://blog.nashcom.de/nashcomblog.nsf/dx/more-strict-server-certificate-handling-in-ios-13-macos-10.15.htm?opendocument&comments
Create an openssl cnf file
First you need a new conf file with the needed new entries required by Apples stricter certificate requirements https://support.apple.com/en-us/HT210176
The new requirements are the extendedKeyUsage and subjectAltName settings
# create test.cnf with this contents
[req]
distinguished_name = req_distinguished_name
x509_extensions = v3_req
prompt = no
string_mask = utf8only
[req_distinguished_name]
O = Toggen
OU = Home
CN = testwms
[v3_req]
keyUsage = keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = testwms
IP.1 = 127.0.0.1
Then with the above config file you can generate a cert that will work using the following command. Warning! this command is for my cups configuration and overwrites the current cert but it might be best to backup your cups dir and then copy the cert and key in manually
Generate your new certs
openssl req -new -x509 -keyout /etc/cups/ssl/62745392ddb7.key -out /etc/cups/ssl/62745392ddb7.crt -days 700 -nodes -config test.conf
Here is the output from a 'working' self-signed cert
root@62745392ddb7:/etc/cups/ssl# openssl x509 -in 62745392ddb7.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
4b:3d:8b:b1:25:16:7a:f8:ea:be:44:55:18:81:06:fd:31:6e:2b:d1
Signature Algorithm: sha256WithRSAEncryption
Issuer: O = Toggen, OU = Home, CN = testwms
Validity
Not Before: Dec 13 06:11:43 2019 GMT
Not After : Nov 12 06:11:43 2021 GMT
Subject: O = Toggen, OU = Home, CN = testwms
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b1:1a:55:18:86:8e:dc:f4:95:d5:b3:3a:c8:98:
6d:9e:1e:43:f7:5f:8a:58:de:da:ee:b1:e1:ec:c4:
db:9f:d1:12:a5:45:ae:5a:f7:63:7b:d1:d6:8d:81:
66:ce:56:8d:f9:67:be:e4:22:ce:06:64:0e:2d:7f:
63:bf:e4:11:f7:e7:5d:62:a1:dc:c0:2f:c4:d4:0c:
d6:7e:be:dd:91:3f:ef:68:bf:29:13:ad:2a:60:41:
9c:a7:f0:f8:89:8c:63:93:2a:62:77:de:09:71:82:
41:8b:8c:33:84:5c:fc:e8:f3:92:e3:c3:56:f2:a2:
c6:a3:e6:bd:10:7c:7d:bb:3e:ae:d6:a7:52:98:28:
aa:3b:98:12:bd:f1:2f:0b:94:82:d4:25:03:5a:1f:
31:f9:fb:38:46:ed:9b:b3:0f:7e:c5:f0:71:05:dd:
af:52:08:3a:44:c3:4d:dd:d1:19:a1:f3:06:2a:3b:
b1:8c:3a:46:96:11:44:ab:2e:33:c3:1a:50:1e:5d:
c3:c7:7e:20:22:4e:2c:17:8e:16:b9:69:02:60:57:
2b:c5:a5:66:f1:5b:15:09:d6:25:db:26:18:5a:a3:
f8:b5:e7:54:b9:82:cc:53:2f:c1:25:42:46:9d:e3:
ee:8e:38:b5:e9:42:38:14:35:f7:aa:9d:67:e5:bb:
39:65
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage:
Key Encipherment, Data Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Subject Alternative Name:
DNS:testwms, IP Address:127.0.0.1
Signature Algorithm: sha256WithRSAEncryption
21:24:49:e8:8b:99:71:0d:13:ee:0f:01:5c:2c:a8:37:53:30:
cb:7d:92:62:43:c5:78:e5:0c:7f:b1:66:63:1e:04:89:80:27:
10:c5:73:0f:0c:8f:80:cd:6f:76:e1:8b:74:ba:71:75:06:db:
90:1a:ed:e9:93:69:5d:bd:5e:dc:90:0f:99:54:50:02:96:20:
74:f7:a5:7b:53:f2:db:01:ea:b2:2e:fe:af:3c:d4:a6:e8:b9:
ea:71:86:4e:9c:83:dc:6c:5e:ac:dd:3b:dd:e3:1f:30:03:c0:
6c:a4:90:50:00:b2:8c:37:09:f1:c3:3d:f5:d8:8f:c0:fa:48:
4a:2a:99:d6:72:3c:b7:7a:33:0b:47:82:8b:a2:48:ff:d3:73:
5a:41:82:2e:58:f1:55:19:4f:5e:22:cc:7b:b1:dd:10:1c:aa:
26:c8:65:45:4f:5a:83:1c:e2:61:d0:06:d1:d7:65:01:f3:9b:
17:18:7c:4e:e3:39:33:76:8b:0e:2a:3c:cf:79:1d:6e:66:da:
33:f0:05:ce:70:28:0c:d8:fa:c1:22:21:40:47:f6:77:ae:14:
22:b9:84:0a:00:c7:91:37:2a:fd:63:57:7c:dc:84:61:c9:c2:
b9:91:56:98:ca:77:3c:0f:a8:62:4b:d2:21:0e:1d:2d:e1:19:
89:6c:60:0b
Note the new sections:
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Subject Alternative Name:
DNS:testwms, IP Address:127.0.0.1
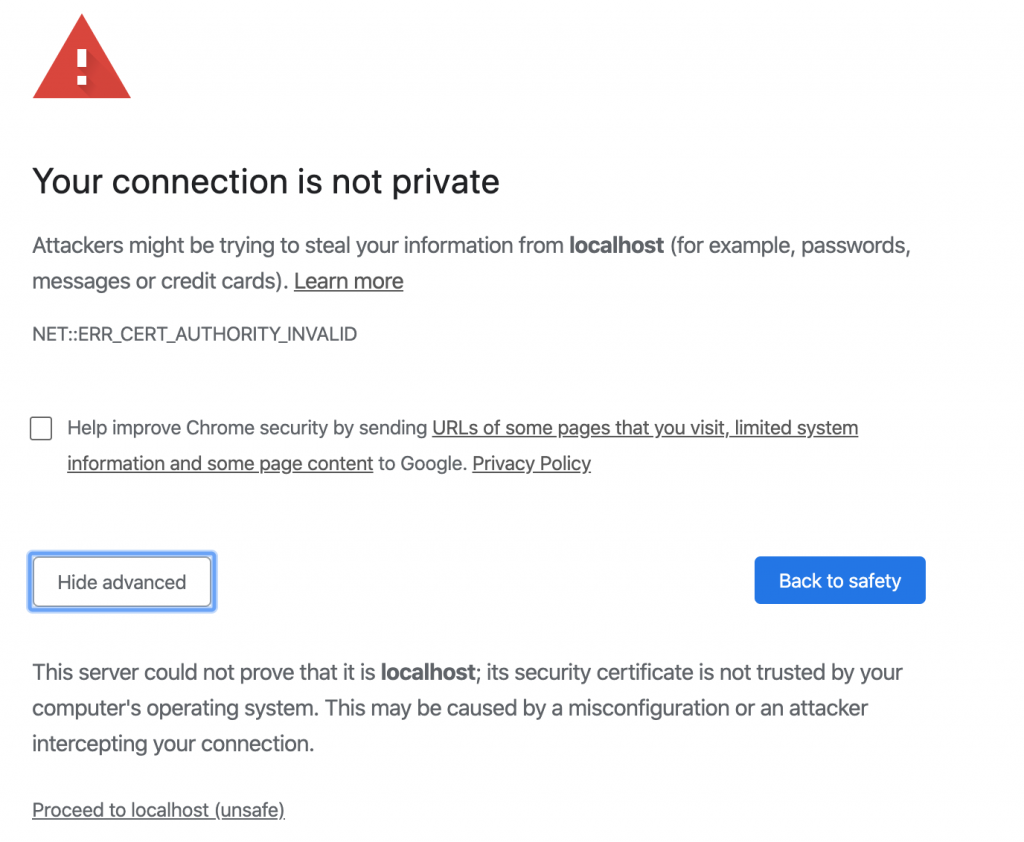
So now when you connect you will see a NET::ERR_CERT_AUTHORITY_INVALID error but you can then click the advanced button and click the Proceed to <hostname_here> (unsafe) button and access your instance of the Cups admin page

0 Comments