Configuring a remote Unifi USG Firewall to broadcast WOL Packets from a remote site to wake a computer
+-----------------+ +-------------------------+
| Site A | | Site B |
| | | LAN: 10.11.12.0/24 |
| [Linux or WSL |-----It's The Internet Jen-----[Remote USG] |
| | 110.173.182.120 |
| with | | [device to wake |
| wakeonlan] | | MAC: 7b:45:59:71:ad:2f] |
| | | |
+-----------------+ +-------------------------+
- At Site A install
wakeonlanon a Linux/WSL box
sudo apt install wakeonlan
- Configure a Port Forward Rule - On the remote site configure the USG to port forward UDP port 9 to an UNUSED IP address e.g. if the remote subnet that computer that needs to be woken on is 10.11.12.0/24 and an UNUSED ip address is 10.11.12.20 then forward it to that. To make it more secure make sure the port forward rule is only triggered by traffic from the external IP of Site A. (You can use the Unifi Controller to configure this). When configuring the port forward configure logging so you can see the packets traverse the USG.
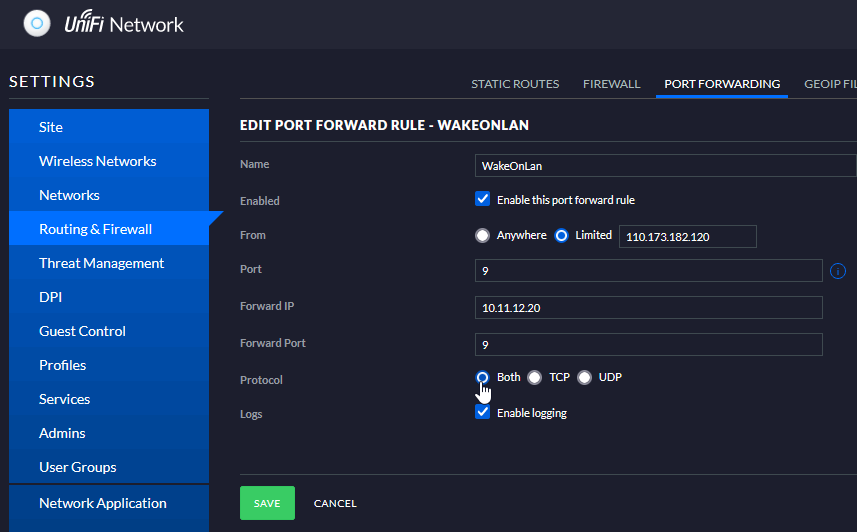
- Login to the remote USG with SSH and then tell it that any traffic sent to 10.11.12.20 should be forwarded to the broadcast address (ff:ff:ff:ff:ff:ff). (To SSH to the USG I usually start a terminal to another Unifi device on the network by clicking that device in the Unifi Controller and then SSH back to the USG)
# on the USG as root
arp -s 10.11.12.20 ff:ff:ff:ff:ff:ff temp
# check it worked
arp -n
# output of arp
# ... other arp table entries
10.11.12.20 ether ff:ff:ff:ff:ff:ff C eth1
# ... other arp table entries continued
- On a Site A Linux box run
wakeonlanto target the external IP of the remote site. Pluggin in the remote external IP of Site B and the MAC address of the Ether Adaptor of the device you want to boot up.
wakeonlan -i 110.173.182.120 7b:45:59:71:ad:2f
How it works explained
The wakeonlan command sends a "Magic" Wake On LAN packet to the external interface of the remote site (in the above example that's 110.173.182.120) the port forward rule configured on the USG will forward the traffic to the unused LAN IP (10.11.12.20) and because the ARP address configured for that LAN IP is ff:ff:ff:ff:ff:ff the Magic Wake On LAN packet will be broadcast to all the Ethernet adaptors on that subnet. The device with MAC address 7b:45:59:71:ad:2f, if it is configured for WakeOnLAN will see that the magic packet matches it's MAC address boot up.
Checking for Successful Arrival of Magic WOL Packets
While logged into the USG via SSH you can check if the packets arrive. Here are two methods
Tailing the messages log
# In the USG SSH session
# tail the messages log
tail -f /var/log/messages
# look for the following output
Jan 31 21:51:38 USG-Firewall kernel: [WAN_IN-3003-A]IN=pppoe0 OUT=eth1 MAC= SRC=110.173.182.120 DST=10.11.12.20 LEN=130 TOS=0x00 PREC=0x00 TTL=53 ID=61121 DF PROTO=UDP SPT=34163 DPT=9 LEN=110
Checking for traffic with tcpdump
root@USG-Firewall:~# tcpdump -i eth1 udp port 9
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
# output example of successful broad cast
22:08:19.031929 IP unifi.40383 > 10.11.12.20.discard: UDP, length 102

0 Comments