I am on a Mac the Microsoft documentation covers Powershell, makecert and Linux instructions for creating Self-Signed certs for the OpenVPN P2S configuration.
However I prefer the familiar and I've used OpenVPN before on Linux and the bundled easyrsa utility included in Debian/Ubuntu makes it easy to create and generate and manage the certs and keys.
So download https://github.com/OpenVPN/easy-rsa/releases and untar the latest EasyRSA
Check out the readme https://github.com/OpenVPN/easy-rsa/blob/master/doc/EasyRSA-Readme.md
cd /to/place/where/you/untarred/easyrsa
cp vars.sample vars
# edit vars
# un comment and modify the following vars
set_var EASYRSA_OPENSSL "/usr/local/Cellar/[email protected]/1.1.1c/bin/openssl"
set_var EASYRSA_REQ_COUNTRY "AU"
set_var EASYRSA_REQ_PROVINCE "Victoria"
set_var EASYRSA_REQ_CITY "Melbourne"
set_var EASYRSA_REQ_ORG "Toggen"
set_var EASYRSA_REQ_EMAIL "[email protected]"
set_var EASYRSA_REQ_OU "Azure Demo OpenVPN"
./easyrsa init-pki
# create a ca.crt
./easyrsa build-ca
# build a client cert
/easyrsa build-client-full client2 nopass
Note: using Easy-RSA configuration from: ./vars
Using SSL: /usr/local/Cellar/[email protected]/1.1.1c/bin/openssl OpenSSL 1.1.1c 28 May 2019
Generating a RSA private key
.....+++++
......................+++++
writing new private key to '/Users/jmcd/Downloads/easy-rsa/EasyRSA-v3.0.6/pki/private/client2.key.DYOAXJrtRM'
-----
Using configuration from /Users/jmcd/Downloads/easy-rsa/EasyRSA-v3.0.6/pki/safessl-easyrsa.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'client2'
Certificate is to be certified until Aug 19 14:51:06 2022 GMT (1080 days)
Write out database with 1 new entries
Data Base Updated
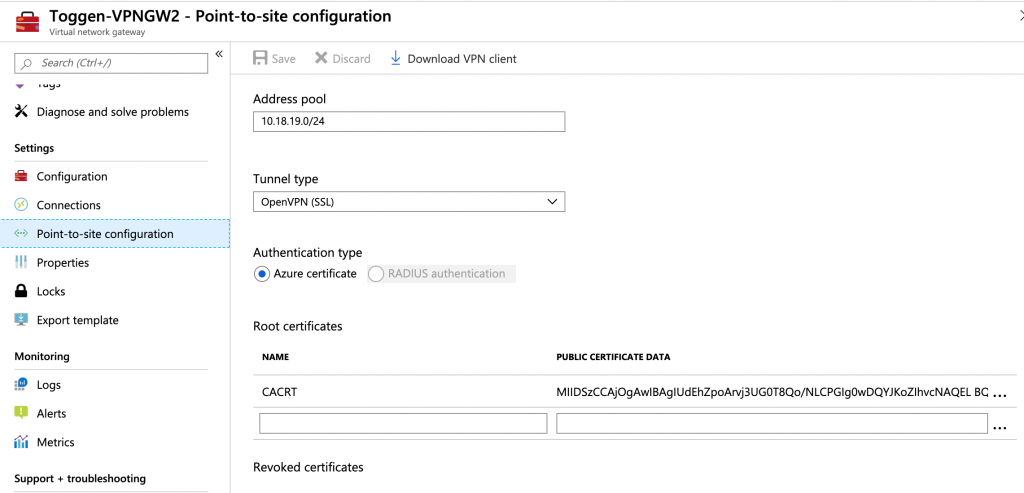
In the Azure portal you add the contents of ca.crt to the Root certificates. NAME is arbitrary and PUBLIC CERTIFICATE DATA is the contents of ca.crt without the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- sections
When you click the Download VPN client button and download the zip containing the ovpn file the certificate copied into the PUBLIC CERTIFICATE DATA field will be in the <ca></ca> section.
This is a copy of the OpenVPN\openvpn.ovpn file that you download when you click the "Download VPN client" button from the azure portal. Everything is standard except for removing the log statement which Tunnelblick doesn't like, and adding the ca.crt, and client.crt and client.key.
client
remote azuregateway-15460063-9c68-4296-8656-84328f96ead2-08086fb9383b.vpn.azure.com 443
verify-x509-name '15460063-9c68-4296-8656-84328f96ead2.vpn.azure.com' name
remote-cert-tls server
dev tun
proto tcp
resolv-retry infinite
nobind
auth SHA256
cipher AES-256-GCM
persist-key
persist-tun
tls-timeout 30
tls-version-min 1.2
key-direction 1
#log openvpn.log
verb 3
# P2S CA root certificate
<ca>
-----BEGIN CERTIFICATE-----
MIIDrzCCApegAwIBAgIQCDvgVpBCRrGhdWrJWZHHSjANBgkqhkiG9w0BAQUFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0wNjExMTAwMDAwMDBaFw0zMTExMTAwMDAwMDBaMGExCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxGTAXBgNVBAsTEHd3dy5kaWdpY2VydC5j
b20xIDAeBgNVBAMTF0RpZ2lDZXJ0IEdsb2JhbCBSb290IENBMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4jvhEXLeqKTTo1eqUKKPC3eQyaKl7hLOllsB
CSDMAZOnTjC3U/dDxGkAV53ijSLdhwZAAIEJzs4bg7/fzTtxRuLWZscFs3YnFo97
nh6Vfe63SKMI2tavegw5BmV/Sl0fvBf4q77uKNd0f3p4mVmFaG5cIzJLv07A6Fpt
43C/dxC//AH2hdmoRBBYMql1GNXRor5H4idq9Joz+EkIYIvUX7Q6hL+hqkpMfT7P
T19sdl6gSzeRntwi5m3OFBqOasv+zbMUZBfHWymeMr/y7vrTC0LUq7dBMtoM1O/4
gdW7jVg/tRvoSSiicNoxBN33shbyTApOB6jtSj1etX+jkMOvJwIDAQABo2MwYTAO
BgNVHQ8BAf8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUA95QNVbR
TLtm8KPiGxvDl7I90VUwHwYDVR0jBBgwFoAUA95QNVbRTLtm8KPiGxvDl7I90VUw
DQYJKoZIhvcNAQEFBQADggEBAMucN6pIExIK+t1EnE9SsPTfrgT1eXkIoyQY/Esr
hMAtudXH/vTBH1jLuG2cenTnmCmrEbXjcKChzUyImZOMkXDiqw8cvpOp/2PV5Adg
06O/nVsJ8dWO41P0jmP6P6fbtGbfYmbW0W5BjfIttep3Sp+dWOIrWcBAI+0tKIJF
PnlUkiaY4IBIqDfv8NZ5YBberOgOzW6sRBc4L0na4UU+Krk2U886UAb3LujEV0ls
YSEY1QSteDwsOoBrp+uvFRTp2InBuThs4pFsiv9kuXclVzDAGySj4dzp30d8tbQk
CAUw7C29C79Fv1C5qfPrmAESrciIxpg0X40KPMbp1ZWVbd4=
-----END CERTIFICATE-----
</ca>
# Pre Shared Key
<tls-auth>
-----BEGIN OpenVPN Static key V1-----
edaa9d2e7cd34a59a80a08d10b1173c0
ed07f33ec56db66e5e8c564ccd895edd
2d48dc5370e02f336772b465155fb1a1
4180dcedb0e1ab5c2f8b3066dff8f101
8a8705e1397f22de66fd1a3c05afcdb2
47717e18a1a5e1b8e4c80413b2f858ca
e774b715b36231a503da49401b882208
3198da18b44b823b268541d4705f7bd7
ab9b62d93686de42a27dcb95bfc920a8
464516f6d8bafe0b3b23924fb8ab9a75
16fc71bda23984d23b79fb4681af0408
db39b3aabd7d541ce99b42f871ecf252
46fe8992e696ca047fe9573b42863185
cce990efffbc6047c995dd9df0040941
8ebdb370548ac0e9ba0d8fbaf6eeeb5d
94777e538fd1b738552fe49568ae0948
-----END OpenVPN Static key V1-----
</tls-auth>
# P2S client certificate
# Please fill this field with a PEM formatted client certificate
# Alternatively, configure 'cert PATH_TO_CLIENT_CERT' to use input from a PEM certificate file.
<cert>
-----BEGIN CERTIFICATE-----
MIIDVDCCAjygAwIBAgIQM51UoKxWZcslb8aHjOFqyjANBgkqhkiG9w0BAQsFADAW
MRQwEgYDVQQDDAtFYXN5LVJTQSBDQTAeFw0xOTA5MDQxMzA0NTRaFw0yMjA4MTkx
MzA0NTRaMBExDzANBgNVBAMMBmNsaWVuMTCCASIwDQYJKoZIhvcNAQEBBQADggEP
ADCCAQoCggEBAKJXkzd84Rh3xhtn/89ucNXM6zKVKTcdyhTsOaCqLRPB06xX2lGb
zrBmM8U4wN9B6rw0nNBhHP10+2KqLcJMxTsT8fGLYjY3aleJ0gOtJQGi3vQhe2fN
ckix/h+b7CmSKZLOtSjD0ssGWSzdLl8oPhTbemHSpomBFeE7i3TDnp2NniTxjXo6
gasr4M4v26oK9MgykxmXEqCDKNQe8ok7qlUghtMVA77c2RwIxC/HAqZAIDd4kO6K
lDN/9Aru+hj4G1XSmQJOhZltf6ACFw4eaBn/RrO6UiX28cRcCS/2FzhQTh40DH0e
RdxUhfD3QcWOdcxLnkjQj1QKnCJ47TNaRAcCAwEAAaOBojCBnzAJBgNVHRMEAjAA
MB0GA1UdDgQWBBSi5fBtPM8A4deX1D660Kf4VC0+yDBRBgNVHSMESjBIgBQ4XPjO
kVXivU/2smkn4xFsMI+SiaEapBgwFjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0GCFHRI
WaaAK7491BtE/EKPzSwjxiINMBMGA1UdJQQMMAoGCCsGAQUFBwMCMAsGA1UdDwQE
AwIHgDANBgkqhkiG9w0BAQsFAAOCAQEAPek25GelYy4K3W4mNmpGRhWVRi88ZGGz
QrAPePmLPTg5rdRJC5ldUk450rHco33jeO9MgAnB0tsHsUeKZk3nd7pQl9+PNicH
S3Za1kXafNFIvcyv6Ku2nth2Rk391mK5xTcLzil91dlgRLGEZztBHidJ2yMwJamn
+JXzeJWozH9oi6DilC5RFlNGk+Ou4KEmrPAr//ZN97WNgeWf8dIQegyeGxAaOwOf
FbS3yKivOyOMnl1UAC/tpFc/NzTHgdNQ17avSiescpceHBfhk5mFoaCGAx3HPE+a
wFQG5uB5RqZ6bg80Tw+X0aP25VX4ouu1ZOXBo8h/J7Bfp5O8FSTupg==
-----END CERTIFICATE-----
</cert>
# P2S client certificate private key
# Please fill this field with a PEM formatted private key of the client certificate.
# Alternatively, configure 'key PATH_TO_CLIENT_KEY' to use input from a PEM key file.
<key>
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQCiV5M3fOEYd8Yb
Z//PbnDVzOsylSk3HcoU7Dmgqi0TwdOsV9pRm86wZjPFOMDfQeq8NJzQYRz9dPti
qi3CTMU7E/Hxi2I2N2pXidIDrSUBot70IXtnzXJIsf4fm+wpkimSzrUow9LLBlks
3S5fKD4U23ph0qaJgRXhO4t0w56djZ4k8Y16OoGrK+DOL9uqCvTIMpMZlxKggyjU
HvKJO6pVIIbTFQO+3NkcCMQvxwKmQCA3eJDuipQzf/QK7voY+BtV0pkCToWZbX+g
AhcOHmgZ/0azulIl9vHEXAkv9hc4UE4eNAx9HkXcVIXw90HFjnXMS55I0I9UCpwi
eO0zWkQHAgMBAAECggEAJonvsu58aViVuQ/ZVJ79PmQlOZ7bZ/A0dv8VNyTvCo+q
9nDsrQ715D5+78TnVJjLZt5+k6FaRnks7GFF96hN8hZsC1FxgTlqj1lyd9j0vgyy
LPZ920iUZtmKYGqdh8jhAa78pq7GLdhV9yaSyZg+FKl9xhdB3ca9MPj3xEJkNzZ0
loTrKlbx3nNn2LBsKnEDP+27NNMDbN3wPKW6/cgWxG5SU5jDpJfhNXaZaiX9Ubb1
49RtZkZLDlvX9nGUlQExT8xa/eOLzL9yOrscujrwLdZZMW0+NWYvnLibl1qeXVAV
j2SIhNfeC4As3aB4eUloJNA9jBAfk0Pb3Udt49OaQQKBgQDN673L2C4u8pLvUL+d
baChXPj7OrZyAZMcy09oP5ebhWqFJEo2YF0cL9EOQesni+tBdihX2ASaaTDsdk4M
WgKzYqc7cG9PC1c+OVHOT+m7i/o+E/aihBvRAhNOXcP6oxvHLhASuPO09JLZlUNp
E1JLeajFaVTxccjC20+w1EPKkQKBgQDJ0rLKbpOTfwS3PULhWi2+ySoTClBZigSY
18bTQVR5foGaUQyRMF5FzXNksne44drZgnOlWPBhxbgzrI+icLRW62iH0jNND13I
p5ihpC4eTw5MDv1yk0VPHOmEwIUlXuXTuT8giyDgSuAK1/ICl/FOdBDB9pcq6NDB
IwnarTCBFwKBgALEpYOE/3HwHtuKuVizbZJdvpcZ/fPgY4rijMm4+R/FFl5902WR
vA6x8dyANFoOvnXd0cMEi2NMALVdDcWKvDiPHfJlm4lzfJPAj4H3fwvfYNjOyeT7
Y6hWn83Q4t6OrMPrsZme1N/c3dCA+iwCb3vGQeeNd+/a+Ljt289juxmRAoGBAIxf
x0lzdaO+UfpdWrpBLdYoNuJ9ZvuQOrhQRJNFOksyyVQbEWGewcNNLfiZBRqLxNtK
l8MmxDNNAVy3pkO2nkhifhcSBeqQSIu6vjeXaRhdpjUSrAfYFPn8wxM5kKI4iiQk
EZtCCcDXc1M3dbWGFymZItq199i5jBD5nO4DTdxLAoGBAKgiOhgRgyTk49D1zhc1
AvJqv74BmJ1DXcZ9jaAmmipLNkRafCqVQfxOj/I7XYCa8dkBm9W2oyOlDQDCCpvx
sUMru9prDQswwPZlJd43FkdzdE9VZ+PszejWc/2d/enHZQunpq2+ziGpOUMmMQn0
VLvmVqQ38T217UyFfuMM3+5O
-----END PRIVATE KEY-----
</key>
This is how the bottom section of the OpenVPN\vpnconfig.ovpn file looks before you replace the place holders with the proper cert and key values
# P2S client certificate
# Please fill this field with a PEM formatted client certificate
# Alternatively, configure 'cert PATH_TO_CLIENT_CERT' to use input from a PEM certificate file.
<cert>
$CLIENTCERTIFICATE
</cert>
# P2S client certificate private key
# Please fill this field with a PEM formatted private key of the client certificate.
# Alternatively, configure 'key PATH_TO_CLIENT_KEY' to use input from a PEM key file.
<key>
$PRIVATEKEY
</key>
By the time you read this post I will have deleted all of the above configuration from my Free Trial of Azure.

Hi James,
Thank you for this post, very helpful.
I'm struggling at the moment exporting the private key for the section:
# P2S client certificate private key
# Please fill this field with a PEM formatted private key of the client certificate.
# Alternatively, configure 'key PATH_TO_CLIENT_KEY' to use input from a PEM key file.
$PRIVATEKEY
I'm in the same scenario using a MAC (OpenVPN and Tunnelblick) but I'm not sure how to export the private key to insert in the section above.
Any ideas?
Kind Regards,
Humza