Just getting my mac to connect to an Azure IKEv2 VPN P2S connection using certs generated by EasyRSA
Assuming you have already init'd and created your ca.crt using EasyRSA. See my previous post regarding this.
Format the ca.crt to copy into the the Root Certificate field. This basically outputs the cert in base64 without any line ends. (it's a long string instead of a block). Not sure if this is a big deal as I think the portal strips the new lines..
openssl x509 -in ca.crt -outform der | base64
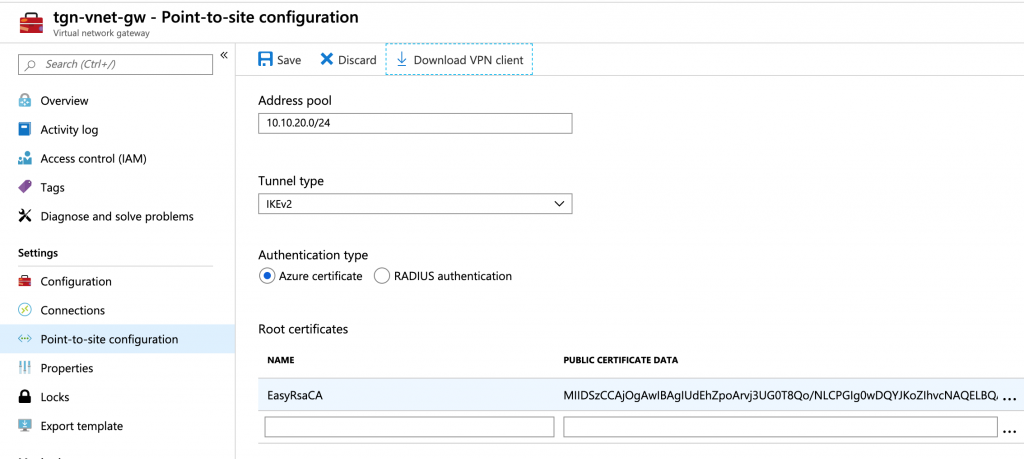
Add the ca.crt to the portal as the Root Certificate
Build some client certs. The export-p12 command bundles the clients private key and public cert together for import into
./easyrsa build-client-full client3
# enter passphrase and make note for client
./easyrsa export-p12 client3
Note: using Easy-RSA configuration from: ./vars
Using SSL: /usr/local/Cellar/[email protected]/1.1.1c/bin/openssl OpenSSL 1.1.1c 28 May 2019
Enter pass phrase for /Users/jmcd/Downloads/easy-rsa/EasyRSA-v3.0.6/pki/private/client3.key:
Enter Export Password:
Verifying - Enter Export Password:
Successful export of p12 file. Your exported file is at the following
location: /Users/jmcd/Downloads/easy-rsa/EasyRSA-v3.0.6/pki/private/client3.p12
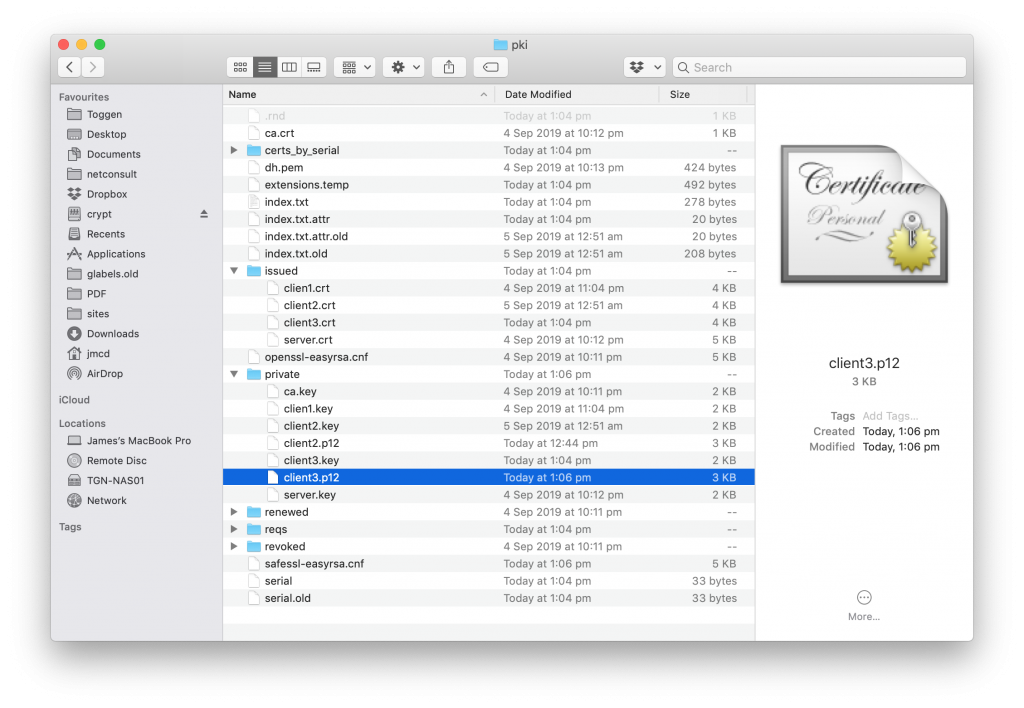
Open the location of you EasyRSA folder and open the pki folder and view the folder structure. Note the ca.crt file and the client3.p12 file in private

0 Comments