The above mentioned question was asked on the Telstra Crowd Support Forums. The reply was "you may find the static IP address route easier". While this is true the static IP from Telstra is an extra $10 dollars a month.
But there is a way to discern the IP Address ranges that Telstra is using to assign an IP Address to your broad band connection, and therefore use them in a firewall rule. See the process as below
Note: This post is in the not recommended for real world use category. If you base your firewall security on accepting IP traffic from Telstra IP Broadband ranges only you will reduce the risk of attack from most of the internet but not eliminate it. Telstra consumer IP ranges may (read "most probably") contain devices that are compromised and sending malicious traffic.
1. Find your external IP Address
Firstly find out what IP address your broadband connection. I usually do this by Googling "What is my ip address"
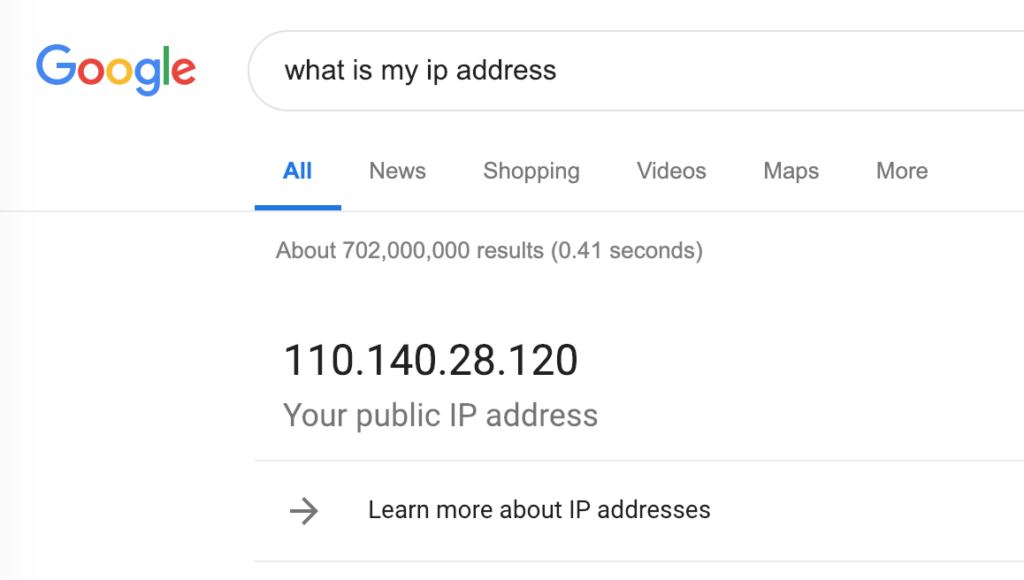
2. Do a whois lookup on your IP
Goto https://www.ultratools.com/tools/ipWhoisLookupResult?
Take the IP address of your connection and enter it into a lookup tool
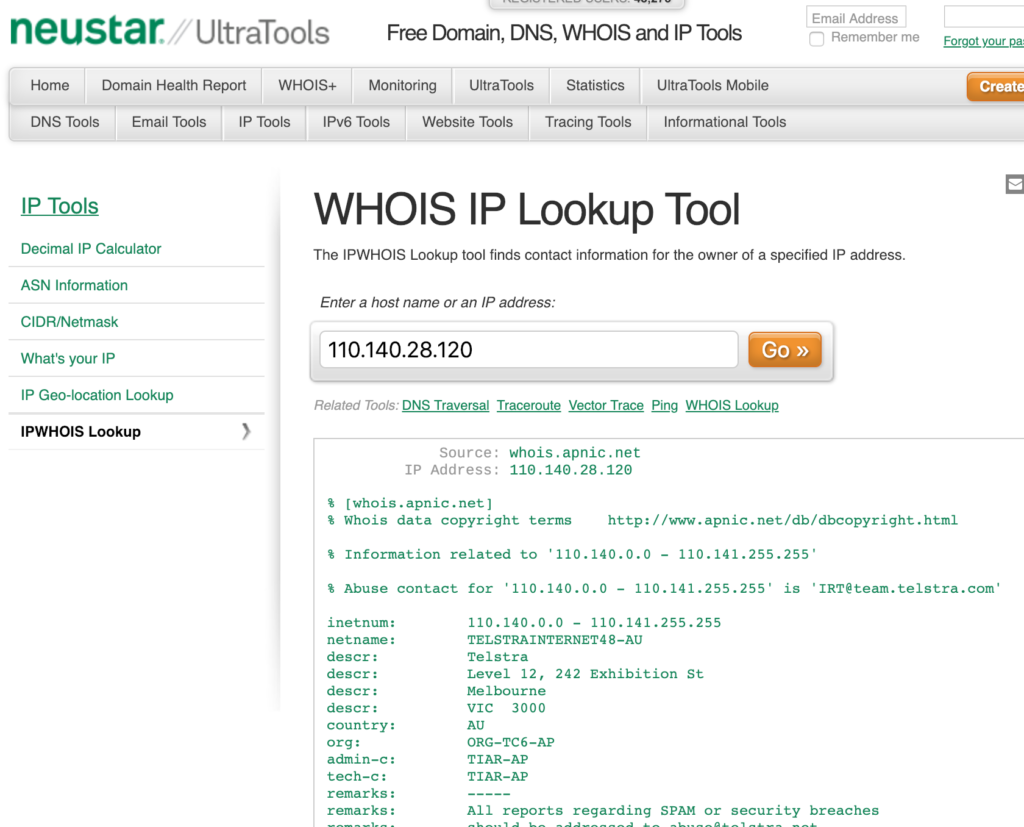
Once you have done the lookup search for the inetnum entry: In this case it contains the IP Address Range of 110.140.0.0 - 110.141.255.255
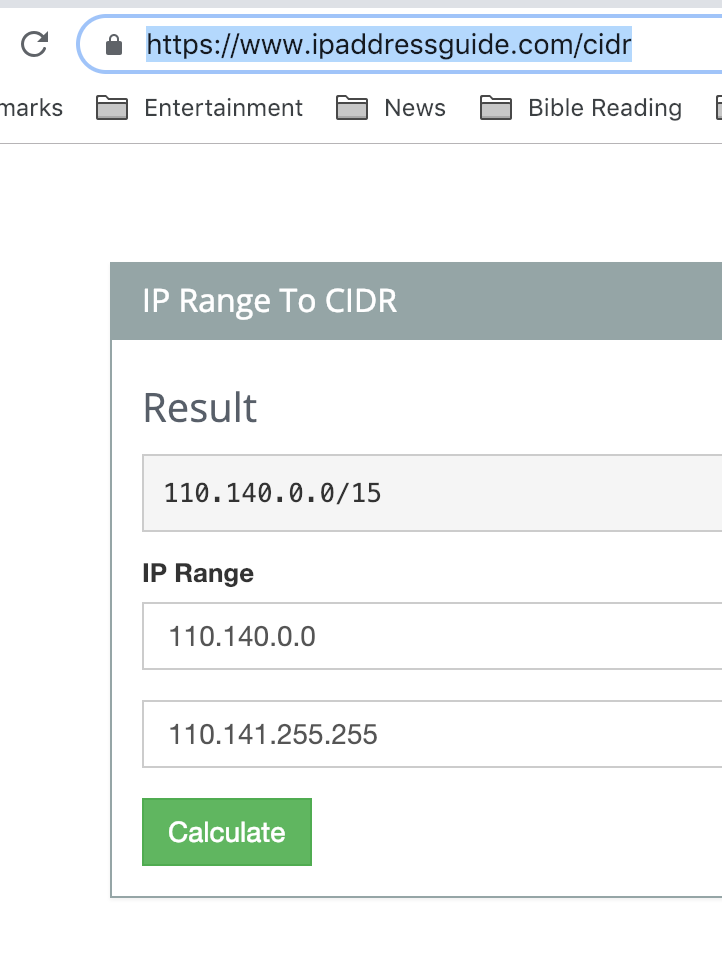
3. Convert the inetnum range to CIDR for use in firewall rules
Go to somewhere that can convert IP ranges to class inter-domain Routing format
From now on you can use the 110.140.0.0/15 in your firewall rules
4. Use the CIDR range to create filtering rules in your security software
Here is an example of using the CIDR into a firewall ruleset in an Amazon Web Services Security Group.
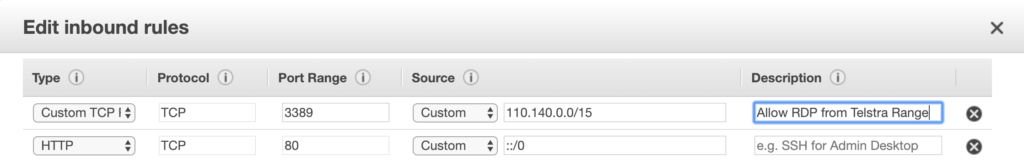
It should be noted that using a /15 range to filter traffic still allows for around 131,072 internet connected devices to access what ever you are trying to protect.
So in conclusion it would be better to have a fixed IP address and use that, but reducing the attack surface from 4 billion to ~131,072 is still better than nothing.

0 Comments