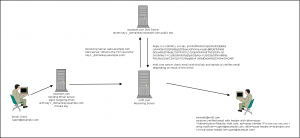
Disclaimer: This is just what I've gleaned from Google and trial and error. So I'm not sure if the following is entirely true but this is how I imagine DKIM works. See http://dkim.org for more information
A person with an email address of [email protected] wants to send an email to [email protected] so he composes one in his favourite mail editor. When he clicks send the email is submitted to an SMTP server if this server is configured for DomainKeys Identified Mail using opendkim it looks up the domain name of the senders address using the from: header in the email envelope and then searches the /etc/opendkim/SigningTable for an entry for that email address or domain.
[email protected] key1._domainkey.example.com *@example.com mail._domainkey.example.com
Finding that there is a specific entry for the [email protected] email address opendkim then takes the key1._domainkey.example.com value and looks up the /etc/opendkim/KeyTable file to find the private key needed to sign emails from [email protected]
mail._domainkey.example.com example.com:mail:/etc/opendkim/keys/example.com/mail.private key1._domainkey.example.com example.com:key1:/etc/opendkim/keys/example.com/key1.private
OpenDKIM finds an entry pointing to /etc/opendkim/keys/example.com/key1.private for key1._domainkey.example.com and uses this private key to sign the email. By default OpenDKIM gathers the date: from: to: subject: headers from the email and the email body and uses these as the basis to create a signature combined with the private key.
Headers:
date:Mon, 1 Sep 2014 01:41:46 -0400
from:[email protected]
to:[email protected]
subject:Test to me at home
Body:
This is a test
Signature of headers plus body:
dkim-signature:v=1; a=rsa-sha256; c=relaxed/relaxed; d=deborahhartl.com; s=default; t=1409550108; bh=B4Sdwm/LsvO9X1e98hS643RXXxvU5oFkgjJHmUF8s3k=; h=Date:From:To:Subject; b=
OpenDKIM then adds a header to the outgoing email:
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=example.com; s=key1; t=1409550108; bh=B4Sdwm/LsvO9X1e98hS643RXXxvU5oFkgjJHmUF8s3k=; h=Date:From:To:Subject; b=qfsbW7o1r4gRh0D4LJq2EGsPzA/m3NLjzvDpiXuTavl6v4lFt2Eb3PoIUY8xtJyMb USupVmew05jFz3cD4HG7MsSBUO8x4mcMBxORkZYCVenuTa7e2FNac1XpUXAkr9atpj 4CuH9aHN2hYaAqbJt+K3uFXqZu0wCQU1MnQOwiF8=
When the email arrives at the destination email server it recognizes that there is a DKIM-Signature head and that the domain is example.com and the selector is key1. It then create a DNS lookup to query the TXT value of key1._domainkey.example.com
The DNS server if it contains the proper record replies with the public key that compliments the private key that the email was signed with
# dig -ttxt +short key1._domainkey.deborahhartl.com "v=DKIM1\; k=rsa\; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDf3owUGPVAnq+lasExBRE/BTi/MAWQOLwWojOYbopr/2cHTI6lCYL1QOaJhOXKAx8TnOql2zP+Qt/xOdVlWy7+Cu0bO9r6P/rhjqfp/VDb/HJ+VL8/SDb/SFNXr88hpP81/NzUJOeKC3oFQLf431iWaqBSn41W8dDe9oMdZDIHFwIDAQAB"
The destination email server then checks that the arriving email has a good signature value by making a check of the headers (h=) specified in DKIM-Signature and body and then adds it's own results header, and accepts to the inbox, accepts and places in Junk/SPAM or rejects the message depending on how strict the policy is of the receiving email server.
Authentication-Results: mx.google.com;
spf=pass (google.com: domain of [email protected] designates xxx.xxx.xxx.xxx as permitted sender) [email protected];
dkim=pass [email protected]
And here is a picture
Refs: Explanation of the DKIM-Signature Header

0 Comments